One solution "triggered updates" to the problem in
a) is given below.
"Triggered updates simply add a rule that whenever a
gateway changes the metric for a route, it is required to send
update messages almost immediately, even if it is not yet time for
one of the regular update message. (The timing details will differ
from protocol to protocol. Some distance vector protocols,
including RIP, specify a small time delay, in order to avoid having
triggered updates generate excessive network traffic.) Note how
this combines with the rules for computing new metrics. Suppose a
gateway's route to destination N goes through gateway G. If an
update arrives from G itself, the receiving gateway is required to
believe the new information, whether the new metric is higher or
lower than the old one. If the result is a change in metric, then
the receiving gateway will send triggered updates to all the hosts
and gateways directly connected to it. They in turn may each send
updates to their neighbors. The result is a cascade of triggered
updates.
It is easy to show which gateways and hosts are involved in the
cascade. Suppose a gateway G times out a route to destination N. G
will send triggered updates to all of its neighbors. However, the
only neighbors who will believe the new information are those whose
routes for N go through G. The other gateways and hosts will see
this as information about a new route that is worse than the one
they are already using, and ignore it. The neighbors whose routes
go through G will update their metrics and send triggered updates
to all of their neighbors. Again, only those neighbors whose routes
go through them will pay attention. Thus, the triggered updates
will propagate backwards along all paths leading to gateway G,
updating the metrics to infinity. This propagation will stop as
soon as it reaches a portion of the network whose route to
destination N takes some other path."
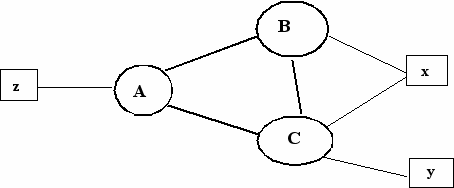 Network x, although connected to two
provider networks, doesn't want to relay packets between those
networks. The service providers relay traffic from other service
providers only to their own customers. For example network X wants
from A only that traffic going to x, but doesn't not want to relay
traffic going to y.
Network x, although connected to two
provider networks, doesn't want to relay packets between those
networks. The service providers relay traffic from other service
providers only to their own customers. For example network X wants
from A only that traffic going to x, but doesn't not want to relay
traffic going to y.