Toisella puolella suomeksi
Toisella puolella suomeksi
Operating Systems II
Final examination 10.1.2006
Write in each answer sheet your name, signature, id-number, course name,
and page nr/total nr of pages
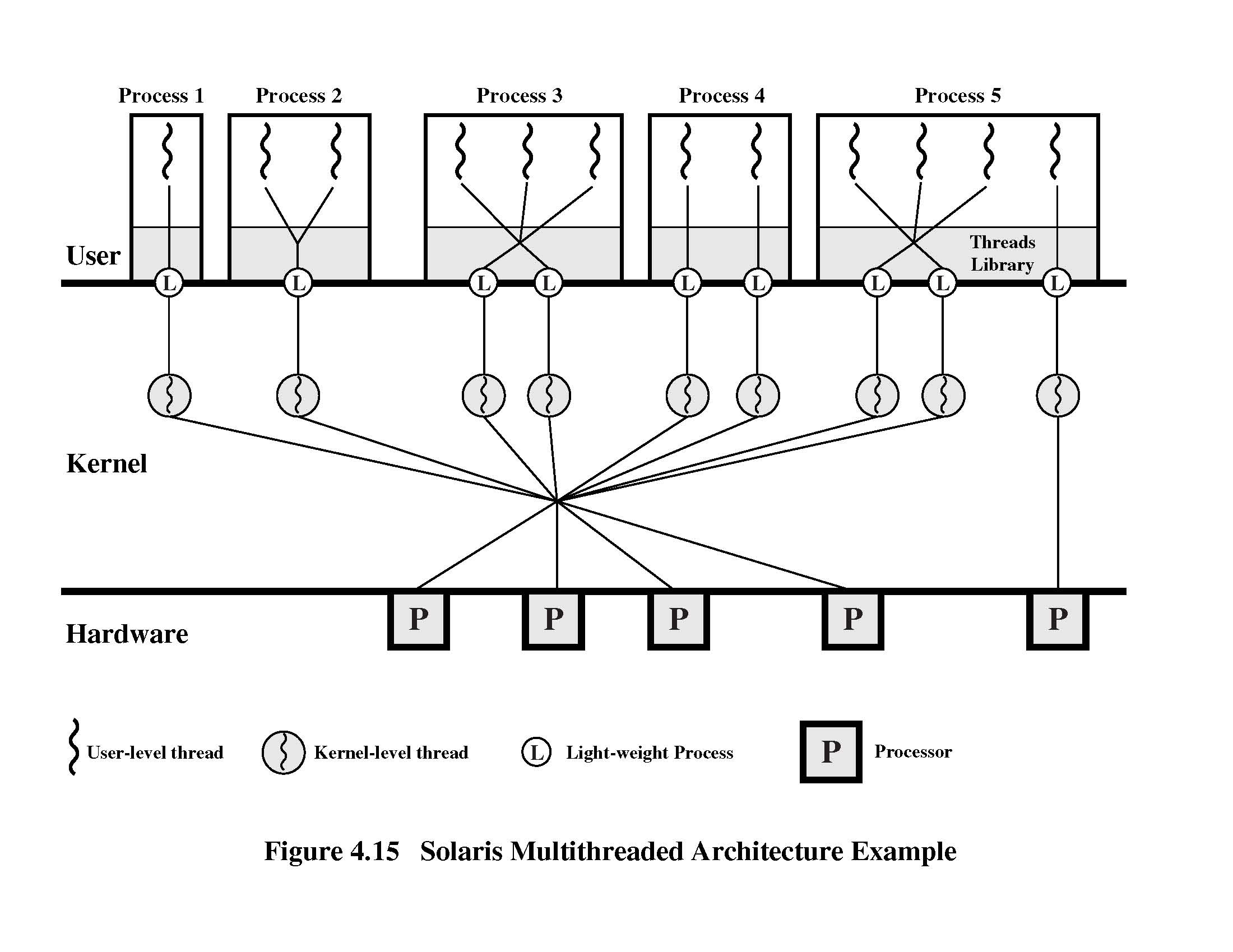
- [15 p] Prosesses and threads. Observe Solaris processes and threads (see
Fig. 4.15 below). Consider two applications: M and K. They all have 8 threads. Application M is of type 3 (with 3 L threads), and application K of type 4 (with 8 L-threads). Assume that the system has 4 processors.
Assume that only of those applications in is executed in the system at any given time.
- [3 p] How many threads can in each case (application M and K) be executing concurrently in machine language level?
- [3 p] If an executing thread will block because of I/O, will the application (M, or K) block or not?
- [4 p] Give an example on an application problem that would be best to solve with similar threads than those of application M, but not with threads similar to application K. Explain. Especially explain why the approach with threads similar to application K would not be sensible.
- [4 p] Give an example on an application problem that would be best to solve with similar threads than those of application K, but not with threads similar to application M. Explain. Especially explain why the approach with threads similar to application M would not be sensible.
- [15 p] Virtual memory Clock page replacement algorithm (max 2 pages).
- [15 p] Process and thread scheduling
- [4 p] How does Feedback q=2i scheduling algorithm
work? For what execution environment is it designed for? Give an example.
- [4 p] How does Fair Share scheduling algorithm
work? For what execution environment is it designed for? Give an example.
- [3 p] How does Gang scheduling
algorithm work? For what execution environment is it designed for?
Give an example.
- [4 p] How does Rate Monotonic scheduling algorithm work?
For what execution environment is it designed for? Give an example.
- [15 p] Security. Explain the following system security requirements and how they can be implemented in the operating system. Give a concrete Linux or Windows example.
Give your answer to only five (5) parts below. If you answer to more than six parts, the only the six worst answers will be graded.
Security requirements: Controlled access to data, Secure use of the system, Secure data transter between systems, Secure file usage, Data confidentiality, Data integrity, Data availability, User authenticity