Operating Systems II (Figures
on reverse side)
Course examination 11.5.2005
Write in each answer sheet your name, signature, id-number, course name,
and page nr/total nr of pages
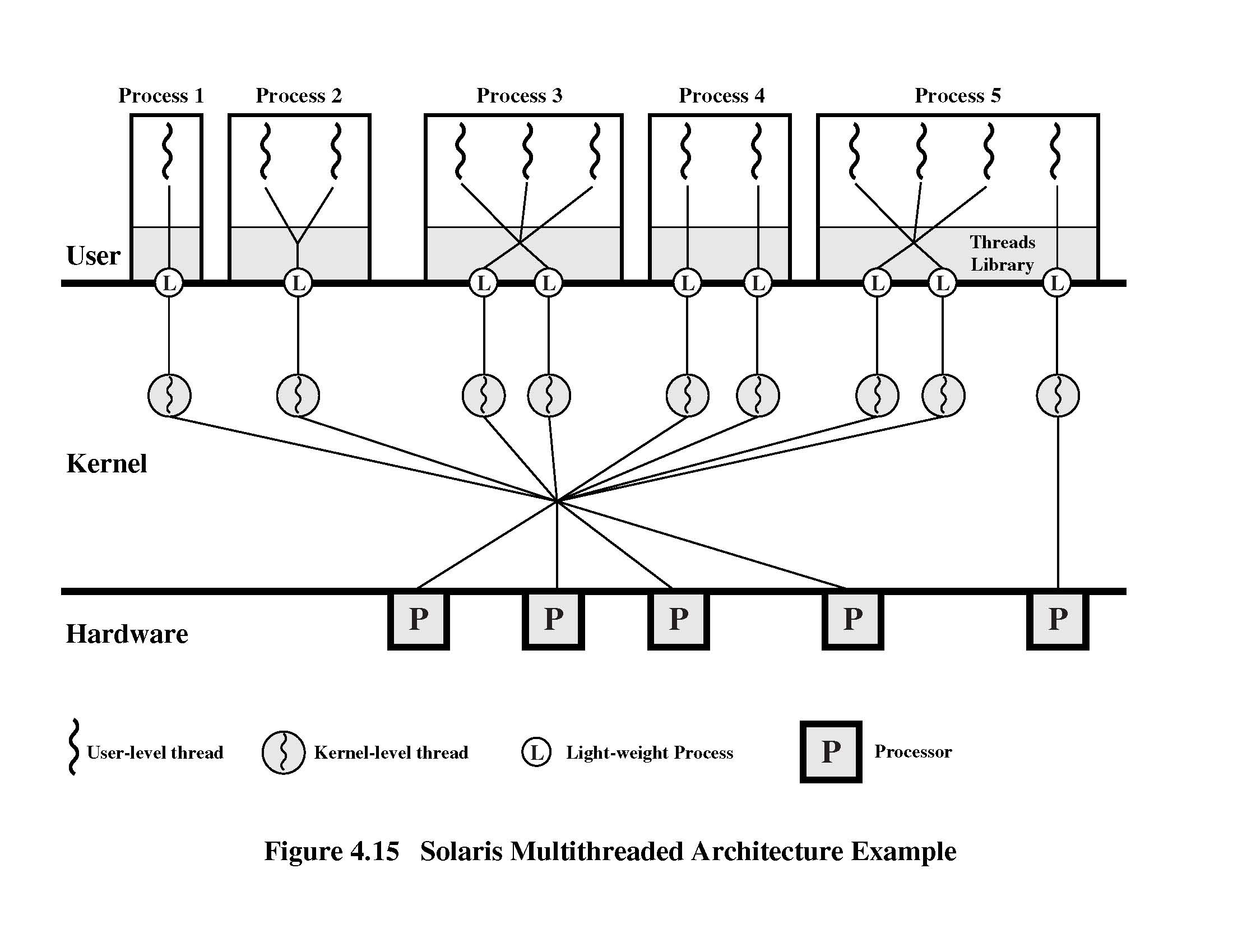
- [13 p] Prosesses and threads. Observe Solaris processes and threads (see
Fig. 4.15 on reverse side). Consider three applications: U, M and K. They all have 8 threads. Application is of type 2 in Fig. 4.15 classification, application is
of type 3, and application of type 4. Assume that the system has 2 processors.
Assume that only of those applications in is executed in the system at any given time.
- [3 p] What operating systems support do the threads of those applications
need for critical section (mutex) synchronization?
- [3 p] How do the threads in those applications communicate with each other?
- [3 p] Who decides and when, which of the threads in those applications is scheduled to processor next.
- [4 p] Give an example on an application problem that would be
best to solve with similar threads than those of application M, but not with threads similar to applications U or K. Explain. Especially explain why the approach with
threads similar to applications U or K would not be sensible.
- [13 p] Linux ext2fs file system
- [3 p] What is an inode and what information does it have?
- [3 p] What is a hard link and how is it implemented in this system? What advantages/disadvantages do hard links have when compared to soft links?
- [3 p] When disk block size is 1 KB, how does one store a 30 KB file XYZ? How does one find the disk blocks for XYZ?
- [4 p] Compare ext3fs to this system? Advantages? Disadvantages?
- [12 p] Process and thread scheduling
(processor scheduling)
- [3 p] Give an example of a scheduling policy, which works well in batch multiprogramming environment, but not so well in time sharing environment. Explain.
- [3 p] Give an example of a scheduling policy, which works well in time sharing environment, but not so well in real time environment. Explain.
- [3 p] Give an example of a scheduling policy, which works well in real time environment, but not so well in time sharing environment. Explain.
- [3 p] Give an example of a scheduling policy, which works well in multiprocessor system time sharing environment, but not so well in uniprocessor system time sharing environment. Explain.
- [12 p] Security. Explain the following system security requirements and how they can be implemented in the operating system. Give a concrete Linux or Windows example.
Give your answer to only six (6) parts below. If you answer to more than six parts, the only the six worst answers will be graded.
- [2 p] Controlled access to data
- [2 p] Secure use of the system
- [2 p] Secure data transter between systems
- [2 p] Secure file usage
- [2 p] Data confidentiality
- [2 p] Data integrity
- [2 p] Data availability
- [2 p] User authenticity