Operating Systems II (Figures
on reverse side)
Course examination 11.5.2004
Write in each answer sheet your name, signature, id-number, course name,
and page nr/total nr of pages
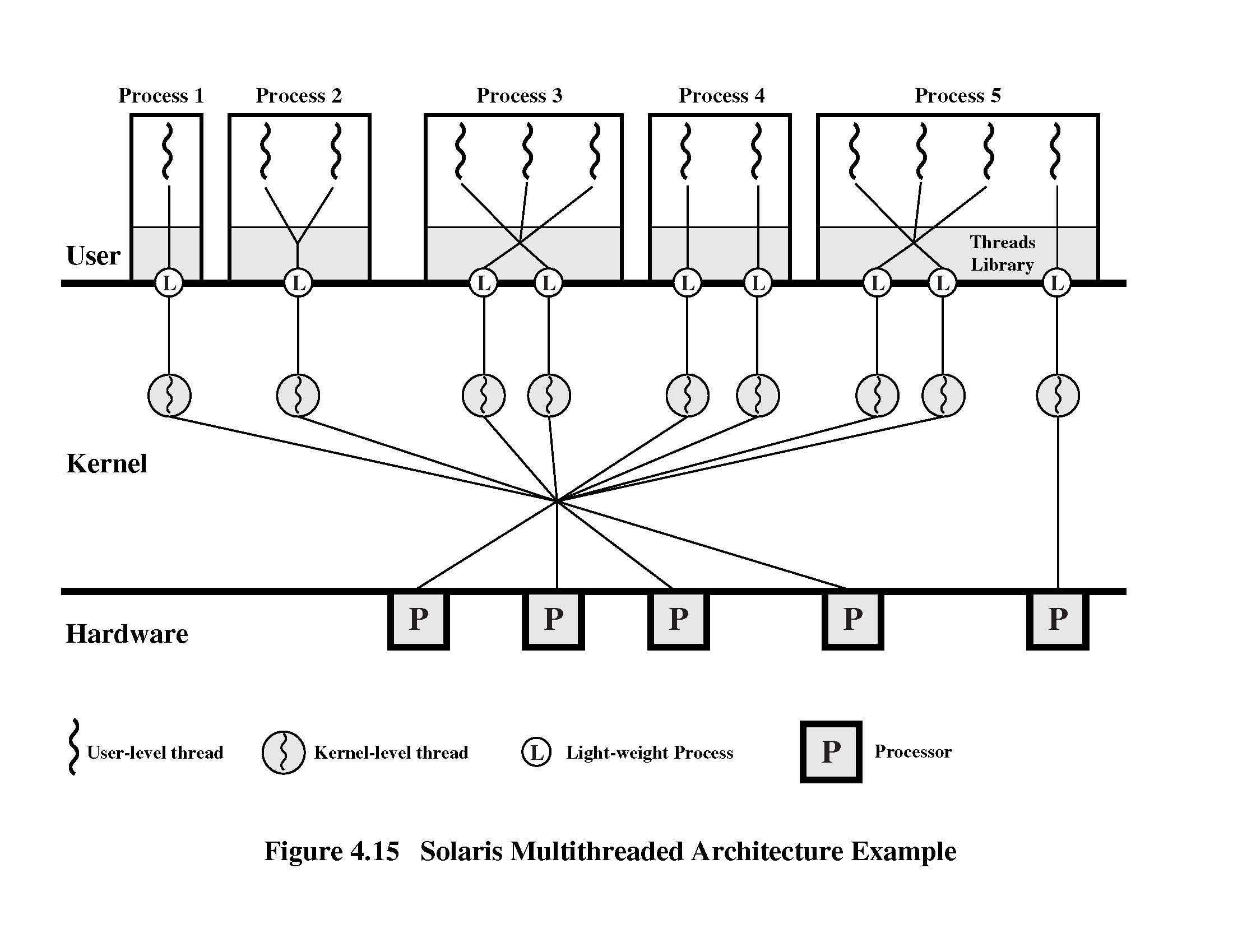
- [13 p] Prosesses and threads. Observe Solaris processes and threads (see
Fig. 4.15 on reverse side).
- [3 p] Explain Fig. 4.15 concepts
- ULT (User Level Thread)
- LWP (Light Weight Process)
- KLT (Kernel Level Thread)
- [2 p] If a ULT is suspended (e.g., waiting for I/O),
then under which circumstances will LWP also suspend?
Similarly, under which circumstances will LWP not suspend?
- [2 p] Explain who schedules ULTs and when.
- [2 p] Explain who
schedules LWPs and when.
- [2 p] Give an example on an application problem that would be
best to solve with similar processes as
process 3 in Fig 4.15
(on reverse side). Explain. Especially explain why the approach with
processes similar to process 4 in Fig 4.15 would not work.
- [2 p] Give an example on an application problem that would be
best to solve with similar processes as process 4 in Fig 4.15 (on reverse
side). Explain. Especially explain why the approach with
processes similar to process 3 in Fig 4.15 would not work.
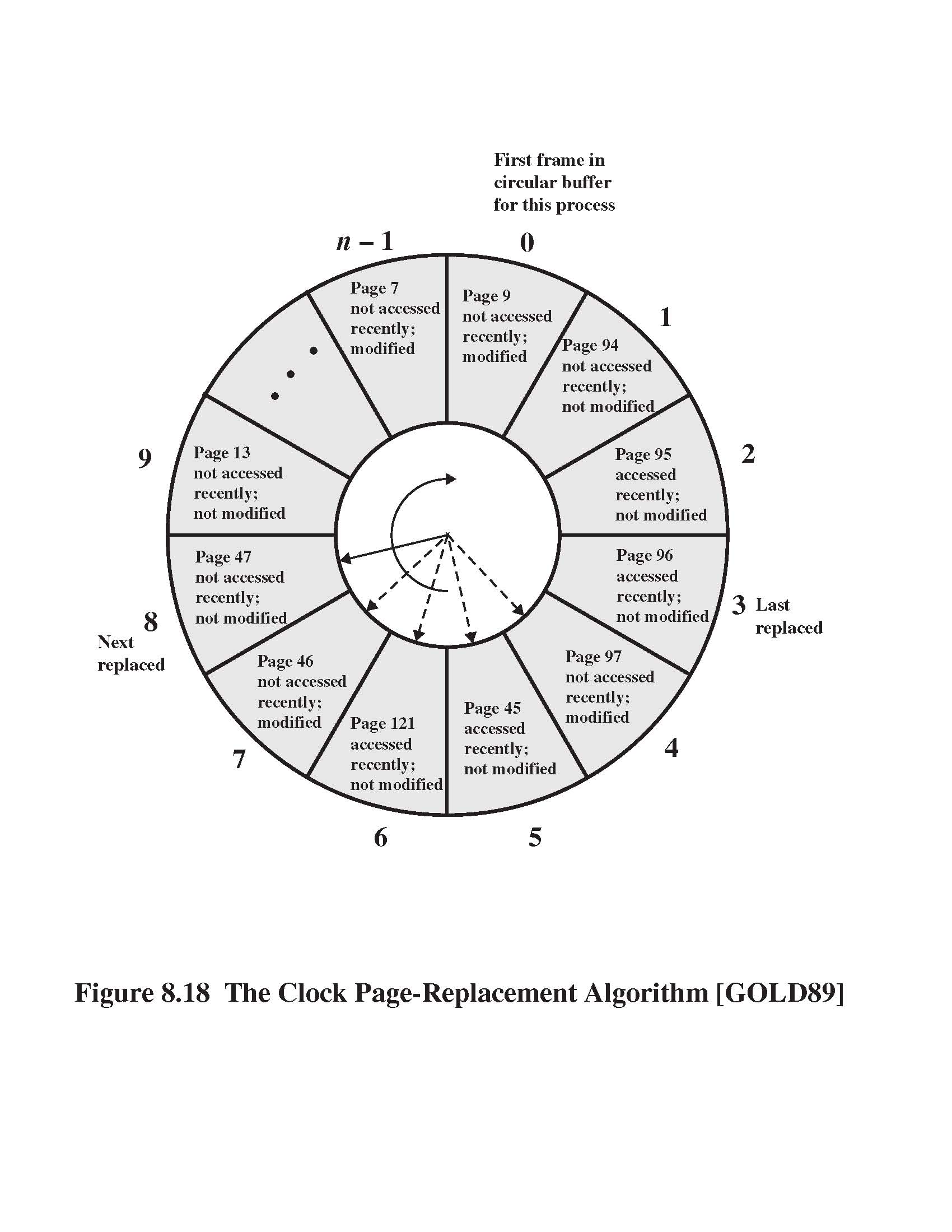
- [12 p] Consider virtual memory Clock page replacement algorithm, when each
page has both R-bit
(viitattu, referenced or accessed recently) and M-bit
(modified). (See Fig. 8.18 on reverse side)
- [3 p] How does Clock page replacement algorithm work?
- [2 p] When is Clock algoritmi activated?
Does it always terminate?
- [3 p] Who sets new values for R- and M-bits and when?
- [2 p] Define concept working set. What has working set to do with this
Clock algorithm?
- [2 p] Is Clock-algorithm local or global page replacement algorithm?
Explain.
- [13 p] Process and thread scheduling
- [3 p] How does Feedback q=2i scheduling algorithm
work? For what execution environment is it designed for? Give an example.
- [3 p] How does Fair Share scheduling algorithm
work? For what execution environment is it designed for? Give an example.
- [3 p] How does Gang scheduling
algorithm work? For what execution environment is it designed for?
Give an example.
- [3 p] How does Rate Monotonic scheduling algorithm work?
For what execution environment is it designed for? Give an example.
- [12 p] Security
- [3 p] How does one implement in UNIX/Linux system the following
situation: user Antti gives user Maijan his game program
GoodGame. When GoodGame is run, it can read and write game file GameLog,
but Maija can not read or write GameLog when she is not playing the
game. Give a detailed example.
- [3 p] What does Trojan Horse security problem has to do with this
situation? Give an example where the problem in part (a) has been solved,
but Antti will gain access to information in Maija's file MyjaPrivate,
to which only Maija has read or write rights.
- [3 p] How can Maija protect herself against the data security attack
given in part (b)?
- [3 p] Is it possible in part (a) solution, that information
in Antti's confidential
file AntiSecret will leak to Maija while she is playing GoodGame. How
or why not? Give an example.